Okay, I understand, we are all busy and have more to do than time to do it. As CRM Administrators we can often spend most of our day reacting to requests with little time to actually plan our response. Here is the typical scenario – The marketing manager calls you and lets you know that […]
Tip #89: Field Level Security and Default Solutions
When you export a default solution from one organization so that you can create a look-a-like in new out of the box organization not everything comes over. Sure we know that users will need the security roles assigned,etc. But this caught me by surprise the other day, I now have it added to our check […]
Tip #80: Auditing for all Critical Records
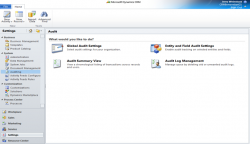
Maybe you don’t want to turn auditing on because you think you don’t need it or are concerned about the additional storage space it will consume. But enabling auditing is a CRM Administrator’s best friend when it comes to understanding the consequences of the assigned security roles. So at the minimum be sure to enable […]
Tip #79: Limit use of System Admin and System Customizer Assignments
At the risk of significant human induced catastrophe, don’t assign the System Administrator or System Customizer security roles to anyone that hasn’t received in-depth training in customizing, configuring and managing the CRM system. No matter how expedient it might be to assign the role to a marketing team member that needs to go into the […]
Tip #78: Business Owner CEO Business Manager

The CEO Business Manager security role in the CRM has broad rights, almost as much as the System Administrator Role. No matter how forcefully you are told, don’t give this role to the owner of the business who is probably also paying the bills. Why? Because most likely, this person is the one that was […]
Tip #77: Security Role Terminology
Before you can create the security architecture or manage your security, you need to know the terms: Privileges are the verbs in CRM: Create, Read, Write, Delete, Append, Append To, Share, Assign. Access levels, from most to least generous: organization, parent-child business unit, business unit, user, none. Entities are the units to which a security […]
Tip #57: Secure Real-time Workflow Execution
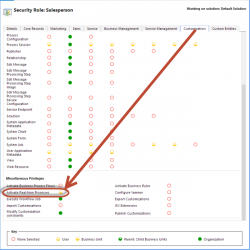
Executing real-time workflows has it’s own security setting. It is in addition to and separate from executing a background workflow. Open up the security role, move the Customization tab, scroll down to Miscellaneous Privileges and assign the appropriate scope.
Tip #29: Solve missing permission issues
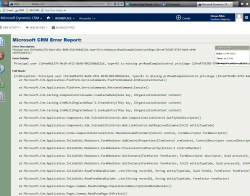
Sometimes, especially when you upgrade CRM or you add new entities, one of your users may see an error message like this: This error means that the user’s security role is missing a permission required for the object they are trying to view or the action they are trying to do. In this example, the […]
Tip #18: How to disable export from the reports
Sometimes there is a requirement to stop users from being able to export CRM reports. Take away Export to Excel privilege and reports will be displayed without the export button. Dependency on Excel export privilege is, perhaps, a bit unintuitive, and the privilege covers not only Excel but other export formats as well. Privilege is […]
Tip #14: CRM Gustronomy – apply security roles to dashboards
System dashboards in CRM 2011 are visible to all users regardless of their roles and permissions. The only supported way to expose dashboard to a selective group of users is to create a personal dashboard and then share it. CRM 2013 added ability to apply security roles to the dashboards making it much easier to […]
 of the
of the