tl;dr
Access Azure blob metadata in two steps: obtain a SAS URI, then make an HTTP request — HEAD to read or PUT to write. Accessing index tags isn’t straightforward; secure a SAS URI that permits tag manipulation elsewhere, then return to complete the task.
Scrumptious if not tedious details
Azure blobs are fast and cost efficient. Just ask any Power Platform admin trying to shoehorn storing 250,000 email attachments in Dataverse — mostly self-proclaiming signatures — into the annual budget, and have a box of tissues ready.
To help manage storage classification and search, blobs have very useful additional features like metadata and index tags. See Manage properties and metadata for a blob with .NET and Manage and find Azure Blob data with blob index tags. Short version: metadata are for additional blob properties (e.g. image EXIF data), while tags are effective classification and search mechanism across containers and blobs.
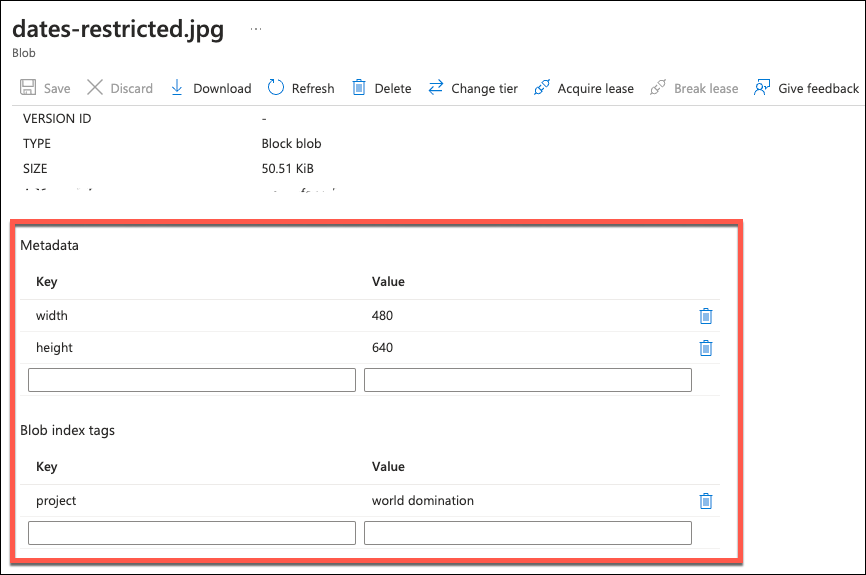
Metadata
Power Automate can easily manipulate blobs using Azure Blob Storage Connector. One cannot be faulted for thinking a method called “Get Blob Metadata (V2)” would return, uhm, metadata. It does return something that looks like a warped version of blob properties but does not contain the actual metadata.
Luckily, metadata is just an HTTP request away: Get Blob Metadata (REST API) – Azure Storage. All we need is SAS key which we can get using the connector: Create SAS URI by path (V2). Request write privilege when creating SAS key and the metadata can be updated as well.
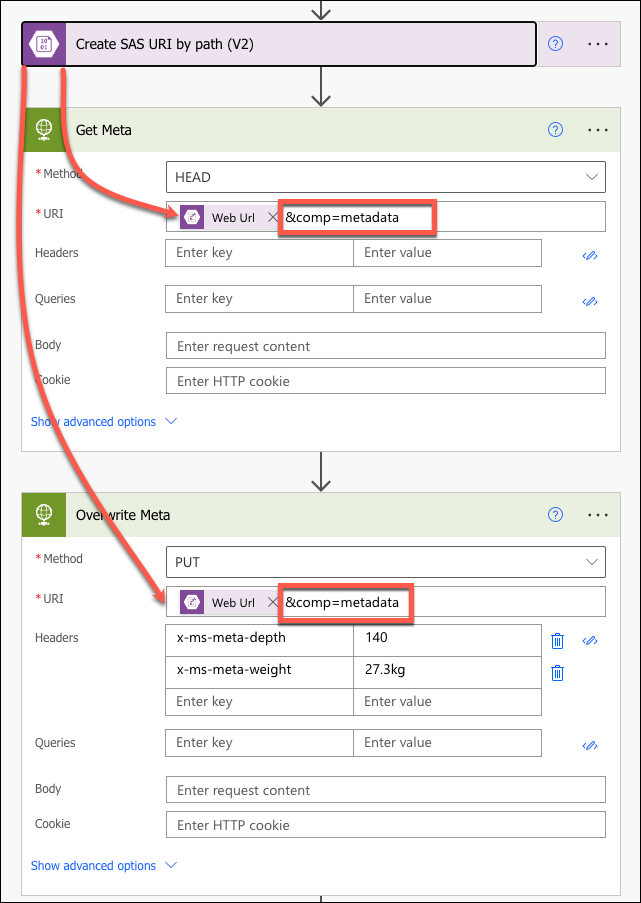
HEAD request returns metadata with the prefix x-ms-meta- as part of the headers block.
{
"statusCode": 200,
"headers": {
"ETag": "\"0x8DC3CABED4F27DF\"",
"Server": "Windows-Azure-Blob/1.0,Microsoft-HTTPAPI/2.0",
"x-ms-request-id": "dfd94108-b01e-0011-620c-832521000000",
"x-ms-version": "2018-03-28",
"x-ms-meta-width": "670",
"x-ms-meta-height": "370",
"Date": "Sun, 31 Mar 2024 01:38:42 GMT",
"Content-Length": "0",
"Last-Modified": "Tue, 05 Mar 2024 00:33:49 GMT"
}
}
Tags
Tags are a little bit more complicated because permissions for tags are governed separately and connector does accommodate them. You can get appropriate permissions baked into the SAS URI using Azure portal, just make sure to add Tags permissions.
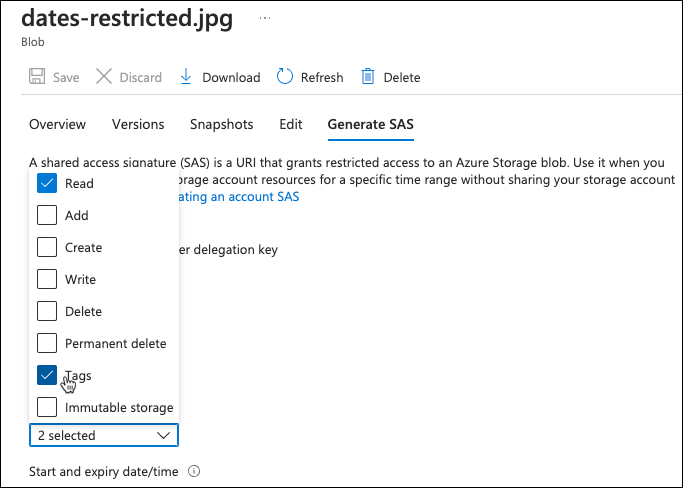
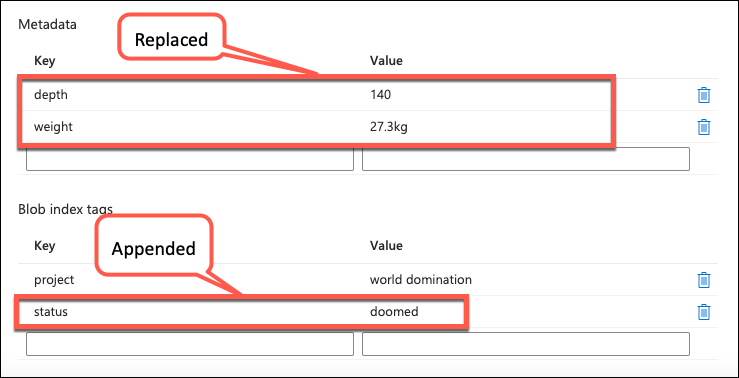
Generated SAS URI can then be used in Power Automate to access index tags. The only difference from the metadata manipulation besides SAS URI and comp query parameter is that we append new tag instead of overwriting (involves a bit of xml manipulation; yes, tags use xml structure).
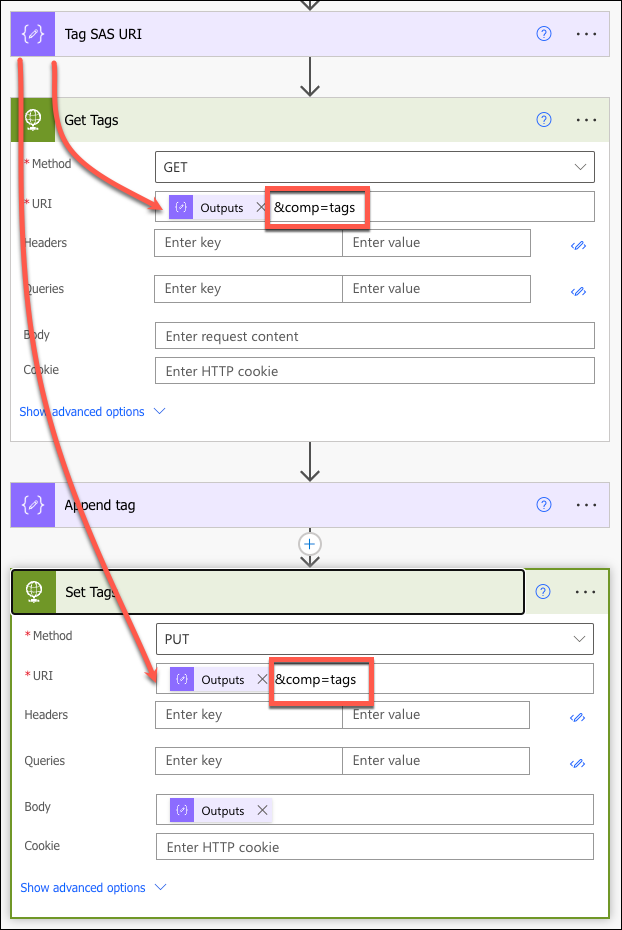
The result:
Would you rather poke the steps yourself? Download the unmanaged solution which includes a sample flow and connection reference.
 of the
of the
Hello, your publication is perfect!!! I was stuck in this type of operation. What type of permission does the web URI have? I tried to update the x-ms-blob-content-disposition and I received :
AuthorizationFailureThis request is not authorized to perform this operation.Thanks for your help
Interesting… Make sure you use
?comp=propertiesin the URL. Then, according to https://learn.microsoft.com/rest/api/storageservices/set-blob-properties, you’ll need Write permission on Set Blob Properties operation on object level.But it gets more interesting. You can bake
content-dispositionupdate into the SAS URL, according to the documentation.Hello George, Thanks for your information. Of course it worked, but by adding ?comp=properties& between the file location and the token of the SAS URL. It works perfectly.
I have a power automate which moves files from dynamics to azure blob
while moving file to azure blob can I set tags?
I can’t set manually as shown above
Generating SaS signatures with tag permissions is not trivial. Your best bet would be to delegate the task to an Azure Function and then use Blob SDK.
I was having trouble authorizing the “Set Metadata” REST API call, but I found a simple solution by using the out-of-the-box Power Automate connector, thanks to this blog.