I’ve created couple scripts that quickly check if your Power Apps portal has a potential vulnerability in the portals I look after.
OData Endpoint Probe
This one is quite trivial and simply probes the OData endpoints exposed by the portal. Takes portal url as a parameter and lists all OData endpoints. Endpoint is marked as a suspect if it can be accessed.

Dataverse Probe
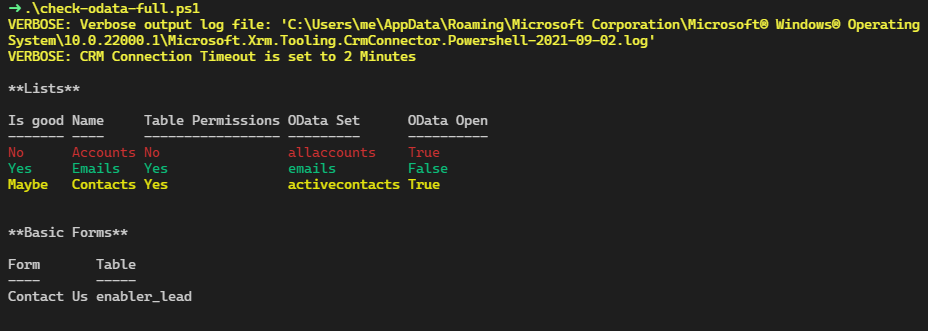
This one is a tad smarter and longer. It prompts to connect to Dataverse, grabs the first portal, and checks lists and forms to see if any of them have table permissions switched off. If permissions are on and endpoint is not accessible, we are good. If permissions are on and endpoint is open it’s a potential leak. If permissions are off and there is an open OData endpoint, this is bad.
For forms it’s black and white: script only lists the forms where table permissions are off.
Consider the chapter about Power Apps portals data leak closed.
 of the
of the