Using service principals is the great way to ensure that Dataverse connections in your Power Automate flows are not user-dependent and nothing is going to break when the original creator’s account gets disabled. These are good step-by-step instructions: How to setup a Common Data Service Application User (and why) (I’ll give Nick Doelman a separate Spießrutenlaufen later on for granting permissions nobody needs).
One of the steps is to create a secret and as of lately, the maximum expiration date can only be up to 2 years in the future. (And no, using custom is not going to help). But what if we want to last longer?
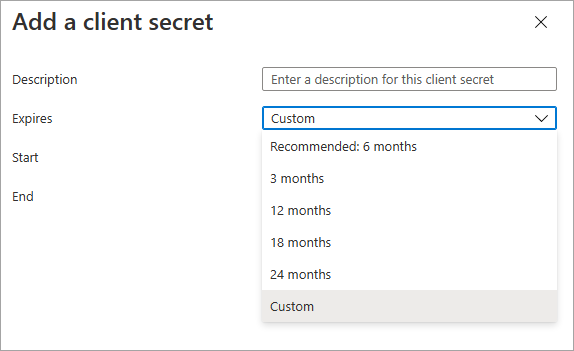
Yes, it’s a good idea to rotate your secrets. No, it’s not a good idea to do so until there are tools to automatically update all connections / connection references in your environment to use the new secret (managed identities / Azure Vaults, anyone?). I was indirectly told that Isaac Stephens figured it all out and it is indeed possible. Turns out, it’s not that complicated.
- Navigate to your app registration in Azure portal. (I trust you know how to do that as you presumably created that registration before, right?)
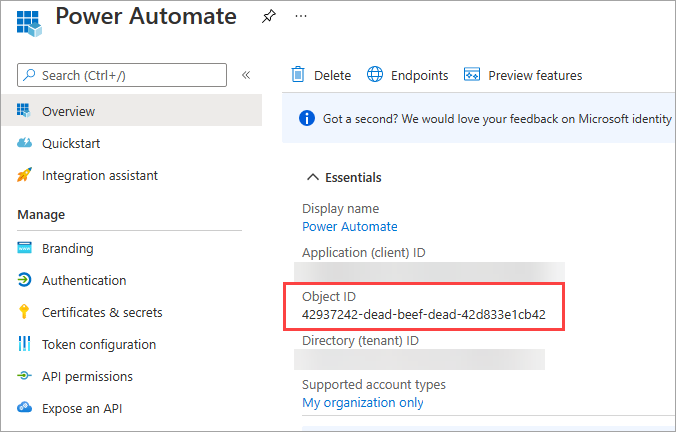
- Get your object id. (I knew it’ll come handy one day!)
- Open Azure CLI prompt and sign in. I like using in-place prompt.
- Enter this command to regenerate a secret that expires in 42 years.
az ad app credential reset --id 42937242-dead-beef-dead-42d833e1cb42 --years 42 - Don’t forget to copy the generated secret from the output – that will be displayed only once!
For additional syntax see az ad app credential | Microsoft Docs.
Cover photo by Osama Elsayed on Unsplash
 of the
of the
[…] the Azure CLI prompt in the Azure portal. As described on Tip #1404 of CRM Tip of the […]
This is a good tip, and of course I agree with the disclaimer that rotation of client secrets and passwords is a good idea. I just wanted to point out that this is not specifically a feature of the CLI. The 2-year limitation is a limitation of the Azure Portal itself. You can also use Microsoft Graph to create a client secret that expires whenever you want (addPassword, it’s called)